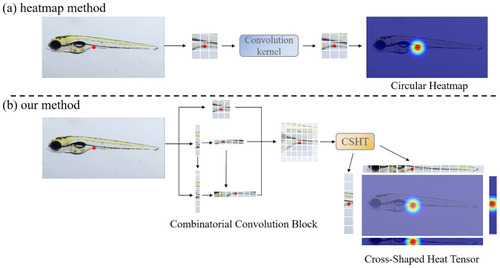
Figure 1
|
Comparison of the conventional keypoint detection framework and ours. ( |